Welcome To Hosting 1
Learn moreWrite About Hosting 1
Hosting 1 is a cutting-edge web hosting provider offering seamless performance and unmatched reliability. It delivers lightning-fast website speeds backed by secure, state-of-the-art infrastructure. With flexible hosting plans, users can easily scale resources to match their evolving business needs. 24/7 expert support ensures any technical issues are resolved quickly and efficiently. Hosting 1 empowers businesses to build, manage, and grow their online presence with confidence.
GAME
Game hosting delivers ultra-low latency, high-performance servers with DDoS protection, global nodes, and one-click mod support for seamless multiplayer experiences.
VPS
A VPS (Virtual Private Server) offers dedicated server-like performance within a shared hosting environment, providing greater control and flexibility. It enables users to customize server settings, install applications, and manage resources independently for enhanced website performance.
Shared
Shared hosting allows multiple websites to use a single server’s resources, making it a cost-effective solution for beginners and small businesses. It offers easy setup and maintenance, though with limited control and scalability compared to dedicated hosting options.
Featured Your Latest Articles
- Xóc Đĩa Online: Hướng Dẫn Toàn…Xóc đĩa online đã trở thành một hiện tượng trong thế giới game trực tuyến tại Việt Nam, đặc biệt là trên nền tảng Đường Đua Đỏ Đen. Trò chơi này không chỉ là một hình thức giải trí mà còn là một phần không thể thiếu trong văn hóa cá cược trực tuyến của … Read more
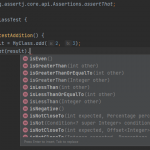
- Writing Effective Java Tests with Assertion…Java has several assertion libraries that can help you with testing and debugging your code. In this article, we’ll look at various assertions libraries and compare them. Overview Test-driven development (TDD) has gained popularity in the last few years. TDD promotes writing tests before developing a functionality, which increases requirement understanding, reduces defects, and decreases … Read more
- Winners of Mathematics Challenge 2024–25 –…Congratulations to the winners of the Lincoln Mathematics Challenge 2024–25 and a big thank you to all participants! A strong competition made the choices difficult for the Competition Committee, and several joint winners had to be chosen for each place. Solutions of the problems can be found here. The results of the competition are: Joint 1st … Read more
- What is VMware NSX? Definition, Features…VMware NSX is a network virtualization feature that allows VMware Cloud Foundation (VCF) subscribers to replicate their entire network infrastructure with software. NSX decouples network functions from hardware by creating a virtual network overlay that emulates physical network components. This allows network architects and engineers who are using VCF to provision and manage network functions … Read more
- What Is Cyber Extortion? How to…Cyber extortion is a crime involving an attack or threat of an attack, coupled with a demand for money or some other response, in return for stopping an attack or preventing one from happening. Cyber extortion attacks involve gaining access to an organization’s systems and identifying points of weakness or valuable targets. Two of the … Read more
- What are pig butchering scams?On Wednesday, June 18, the U.S. Attorney’s Office announced it had seized $225 million in cryptocurrency connected to pig butchering scams. The seizure involves funds stolen from 400 victims worldwide, and as CNBC reports, it’s the largest-ever seizure of its kind. A pig butchering scam is a common type of online scam in which cybercriminals … Read more
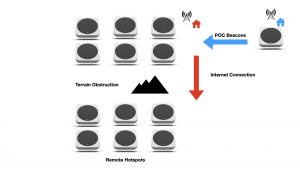
- Updated Antenna Denylist Classifier | Helium…Back in January, we added two new denylist classifiers, the antenna split classifier and the latency classifier. In the time since we’ve identified some shortcomings with the antenna classifier, so we’ve put in some time improving it. The old classifier was rather crude in that we only ever configured it to look for reciprocal (in … Read more
- Unlocking the Power of Packets: Find…Network visibility is enhanced through the time-stamped logs, performance metrics, and end-to-end traces collectively known as telemetry data. Each unique data source provides valuable clues that help IT teams and network engineers resolve issues and maintain performance standards, both locally and in the cloud. When these discreet lanes of information converge with comprehensive and inciteful … Read more
Modern
- Simplifying the Migration from Telco to…As digital technologies advance and consumer demands shift, the global telecommunications industry is rapidly undergoing a transformation. Faster networks and lower latencies are required to support emerging technologies such as IoT networks/systems, AI and cloud computing. As such, telcos are evolving to resemble technology companies, with a focus that extends beyond what a traditional telco … Read more
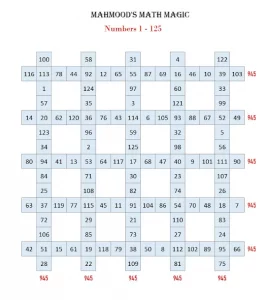
- Math Magic Mystery: New Mathematical Magic…In this special math magic, numbers are in sequence from 1 to 125. Five rows and five columns containing 15 numbers have the same sum of 945. Twenty-five numbers in a different color of each row group have the same sum of 1575. Twenty-five numbers in a different color of each column group have the … Read more
- Cách Đọc Vị Xóc Đĩa OnlineXóc đĩa, một trò chơi cổ truyền của Việt Nam, đã trải qua một cuộc cách mạng khi chuyển sang môi trường trực tuyến. Tại Đường Đua Đỏ Đen, chúng tôi nhận thấy sự hấp dẫn của xóc đĩa online đối với người chơi Việt Nam ngày càng tăng. Trò chơi này không chỉ mang … Read more
- Inside the Frontier of AI, WebXR…KODE Immersive fuses AR, VR, real-time 3D, and spatial computing to craft high-impact, interactive experiences. It’s not just a platform – it’s a portal. Designed to ignite emotion, shatter expectations, and redefine digital engagement. Our challenge? To bring this pioneering vision to life, not just by explaining what KODE Immersive is, but by making visitors … Read more
- IOT Denylist Refinement | Helium DocumentationIn early August Nova Labs posted a change in how the denylist is operated. This change has resulted in several positive effects on the network in terms of the number of hotspots that were improved and cleared from the denylist, as well as clusters of misbehaving hotspots getting turned off, clearing innocent hotspots that were … Read more
Just released
- Simplifying the Migration from Telco to…As digital technologies advance and consumer demands shift, the global telecommunications industry is rapidly undergoing a transformation. Faster networks and lower latencies are required to support emerging technologies such as IoT networks/systems, AI and cloud computing. As such, telcos are evolving to resemble technology companies, with a focus that extends beyond what a traditional telco … Read more
- Math Magic Mystery: New Mathematical Magic…In this special math magic, numbers are in sequence from 1 to 125. Five rows and five columns containing 15 numbers have the same sum of 945. Twenty-five numbers in a different color of each row group have the same sum of 1575. Twenty-five numbers in a different color of each column group have the … Read more
- Cách Đọc Vị Xóc Đĩa OnlineXóc đĩa, một trò chơi cổ truyền của Việt Nam, đã trải qua một cuộc cách mạng khi chuyển sang môi trường trực tuyến. Tại Đường Đua Đỏ Đen, chúng tôi nhận thấy sự hấp dẫn của xóc đĩa online đối với người chơi Việt Nam ngày càng tăng. Trò chơi này không chỉ mang … Read more
- Inside the Frontier of AI, WebXR…KODE Immersive fuses AR, VR, real-time 3D, and spatial computing to craft high-impact, interactive experiences. It’s not just a platform – it’s a portal. Designed to ignite emotion, shatter expectations, and redefine digital engagement. Our challenge? To bring this pioneering vision to life, not just by explaining what KODE Immersive is, but by making visitors … Read more
- IOT Denylist Refinement | Helium DocumentationIn early August Nova Labs posted a change in how the denylist is operated. This change has resulted in several positive effects on the network in terms of the number of hotspots that were improved and cleared from the denylist, as well as clusters of misbehaving hotspots getting turned off, clearing innocent hotspots that were … Read more
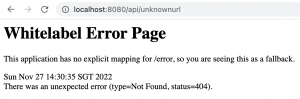
- Disable Whitelabel Error Page in Spring…In this article, we’ll learn how to disable default Whitelabel Error Page in Spring Boot. Whitelabel Error Page Whitelabel error page appears when you hit a url which result into HTTP error. Whitelabel error page is generated by Spring Boot as a default mechanism when no custom error page is found. Let’s hit a wrong … Read more
Newest
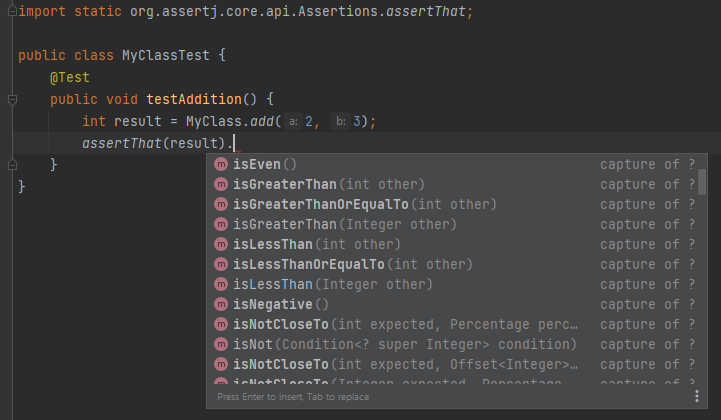
Writing Effective Java Tests with Assertion…
Java has several assertion libraries that can help you with testing and debugging your code. In this article, we’ll look at various assertions libraries and compare them. Overview Test-driven development (TDD) has gained popularity in the last few years. TDD

Baked Lemon Curd Hand Pies
With prepared lemon curd as a filling, these baked hand pies are a snap to pull together. With their bite-size shape and vanilla-scented glaze, it’s hard to resist eating more than one. Baked Lemon Curd Hand

The Science of Audio-Based Revision –…
The Science Behind Audio-Based Learning Do you ever feel like you’re studying for hours but remembering very little? You’re not alone. Many students struggle with inefficient revision techniques that waste time and yield poor results. What if there was a
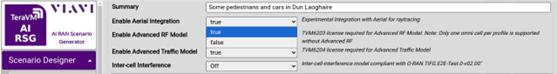
Integrating VIAVI AI RSG with NVIDIA…
At the NVIDIA GTC conference, VIAVI announced it is expanding its TeraVM AI RAN Scenario Generator (AI RSG) product by integrating it with the NVIDIA Aerial Omniverse Digital Twin (AODT). The integration enables realistic and detailed radio access network (RAN)
Journey to 1000 models: Scaling Instagram’s…
In this post, we explore how Instagram has successfully scaled its algorithm to include over 1000 ML models without sacrificing recommendation quality or reliability. We delve into the intricacies of managing such a vast array of models, each with its
Lincoln Mathematics Challenge 2024–25
Lincoln Mathematics Challenge 2024–25 For the honour of winning the competition as 1st, 2nd, or 3rd place winner, submit your typed or neatly written (and scanned in a single pdf file) solutions of the following problems to maths@lincoln.ac.uk with “Maths Challenge”

Enhancing Retry Patterns with a bit…
Operations may fail for transient reasons. How can you implement retry patterns? And how can a simple Jitter help you stabilize the system? Table of Contents Just a second! 🫷 If you are here, it means that you are a
The Kali Linux Phishing Tool
Hello Guys, Today we are going to discuss about how to do phishing in different social media accounts using Hidden Eye. So I am hoping that you have already installed Virtual Box and Kali if not then I will write

Hazelnut brown butter speculaas cookies
I love Dutch speculaas cookies, They are a yummy spiced cookie, sometimes made with ground nuts, but not always. Perhaps it depends on the region. I decided to change them up a little and use ground roasted hazelnuts. I love
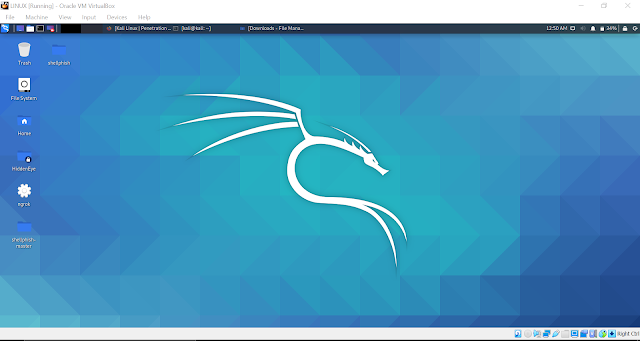
New artist name field on our…
A while ago we made an improvement to how track and artist information is displayed on SoundCloud, making it clearer and easier to understand. Previously, it could be confusing when content wasn’t directly uploaded by the artist. One example might